A compression attack is a type of cyber attack that exploits vulnerability in data compression algorithms to manipulate or steal sensitive information. These attacks can involve using malformed or specially-crafted data to crash or take control of compression software, or using compression to hide malicious code within file formats.
As technology continues to advance, cyber threats are becoming increasingly sophisticated, and compression attacks are just one example of the tactics employed by malicious actors. Understanding the potential risks and taking steps to protect against them is essential for businesses and individuals who want to safeguard their data.
We will explore what compression attacks are, how they work, and strategies for preventing them. By implementing the right security measures, you can help to protect your information and prevent these attacks from causing damage.
What Is A Compression Attack?
Compression Attack is a digital attack that involves compressing a large file to a significantly smaller size, making it easier for hackers to infiltrate or steal information. Cybercriminals launch these types of attacks by using sophisticated algorithms and techniques to compress data and send it through unsecured channels.
Common Types Of Compression Attack
| Type | Description |
|---|---|
| Zlib Compression | Attackers use this type of compression to evade detection from security applications. They utilize a vulnerable compression algorithm to corrupt the file and inject malicious code. |
| Stream-based Compression | This type of compression attack is where cybercriminals use a stream-based compression algorithm to compress and encrypt sensitive data. The compressed data is then sent through unsecured channels, making it easier for attackers to steal the information. |
| Dictionary-based Compression | Dictionary-based compression attacks are where attackers use predefined dictionaries to compress a file’s content. They take advantage of the patterns and repetitions in the data to make the compressed file smaller, making it easier for them to infiltrate the victim’s system. |
How Compression Attacks Work
Compression attacks work by exploiting the vulnerabilities present within the compression process. When a file is compressed, the compression algorithm looks for patterns and repetitions in the data to make the file smaller. Attackers use this process to their advantage by intentionally injecting malicious code into the file, which the compression algorithm compresses along with the data.
Once the compressed file is sent through unsecured channels, the attacker can use a decompression algorithm to extract the malicious code and execute it on their victim’s system. This can result in theft of sensitive data, system hijacking, or installation of malware.
It is crucial for organizations to implement robust security measures, such as using reliable compression algorithms, to mitigate the risk of a compression attack.

Credit: www.masteringthemix.com
Reasons For Using Compression Attacks
Compression attacks are commonly used as a technique to reduce the size of data in order to save bandwidth and storage space. They help in faster data transmission and efficient storage utilization. This makes compression attacks effective for transmitting or storing data in a resource-constrained environment.
Compression Attack In Cybersecurity
Compression attacks are a type of cyber attack that involves compressing files and data in order to reduce the size of the information being transmitted, which can make it more difficult for security systems to detect. These attacks are commonly used in phishing scams, where cybercriminals attempt to trick users into downloading malware or providing sensitive information.
One reason why cybercriminals may choose to use compression attacks is because they can help to bypass certain security measures that are put in place to detect malicious activity. For example, many security systems are designed to flag files and data that are larger than a certain size, which can make it easier to identify suspicious activity.
Compression attacks can also help to disguise the true nature of the data being transmitted. By compressing files and data, cybercriminals can make it more difficult for security systems to identify whether the information being transmitted is malicious in nature or not. This can be particularly effective in cases where the data may not be inherently malicious, but is being used in a malicious way.
Using Compression Attacks In Malware
Another area where compression attacks are commonly used is in malware. Malware is software that is designed to infect a computer or network in order to steal data, corrupt files, or perform other malicious activities. Compression attacks can be used to make malware more difficult to detect, as well as to make it more efficient when it comes to transmitting data.
Many types of malware are designed to communicate with remote servers in order to send and receive data. Compression attacks can be used to reduce the size of the data being transmitted, which can help to reduce the amount of bandwidth that is required to transfer this information. This can make it more difficult to detect the malware, as well as to track the data that is being transmitted.
In addition to this, compression attacks can also be used to make malware more efficient when it comes to transmitting large amounts of data. By compressing the data, cybercriminals can reduce the amount of time and resources that are required to transfer the information from one location to another, which can help to make the attack more effective.
Examples Of Compression Attacks
Compression attack is a type of cyberattack where an attacker tries to exploit vulnerabilities in data compression algorithms to achieve unauthorized access. Some examples of compression attacks are Zip bombs, HTTP response smuggling, and BREACH.
Compression attacks have become increasingly popular in recent years. Attackers use different methods to exploit vulnerabilities within compression algorithms to gain unauthorized access to sensitive data. In this section, we will discuss two common examples of compression attacks – The 7Zip Attack and The RAR Attack.
The 7zip Attack
7Zip is a widely used open-source file archiver that compresses files for storage or transmission. Unfortunately, it is not immune to attack. Attackers can exploit a vulnerability within the compression algorithm and create a malicious archive that contains a file with a name that includes a string of specific characters. When 7Zip is used to unpack the archive, it will crash, allowing the attacker to execute malicious code.
The Rar Attack
RAR is a file archiving software that is used to compress large files. Attackers can exploit a vulnerability in RAR’s compression algorithm by creating a malicious archive. When the victim opens the archive, it executes a file that installs malware onto the victim’s system. This allows the attacker to gain unauthorized access to the victim’s files and potentially their entire network. In conclusion, compression attacks are a serious threat that can lead to significant data breaches and financial loss. It is essential to be aware of these attacks and take steps to protect your systems and sensitive data. Regularly updating your compression software, being suspicious of unexpected archives, and avoiding suspicious websites and downloads are all important precautionary measures.

Credit: www.audio-issues.com
Detection And Prevention Of Compression Attacks
Compression attacks can harm the security of a website, making it vulnerable to hackers. By detecting and preventing these attacks, one can ensure the safety of their website and protect sensitive information from being compromised. With the right tools and techniques, it is possible to mitigate the risks associated with compression attacks.
Compression attacks are yet another form of cyber attack that hackers use to gain unauthorized access to websites. A compression attack involves attackers sending compressed data to the server to overwhelm its resources. The server tries to decompress the data and fails, resulting in a denial-of-service (DoS) attack. In this article, we will focus on how to detect and prevent compression attacks.
Recognizing Signs Of Compression Attacks
Detecting the signs of a compression attack can be challenging, but there are tell-tale signs that can help identify them. One of the most apparent signs is a sudden spike in network traffic. Compression attacks can cause significant spikes in network traffic because of the excessive data the attacker sends. Another sign that may indicate a compression attack is a sudden increase in resource utilization. If you notice any of these signs, you should notify your web administrator immediately so they can investigate further.
Preventing Compression Attacks
Preventing compression attacks largely involves mitigating the attack and protecting the server from being overwhelmed. One of the most effective ways to prevent compression attacks is to configure your server to limit file sizes. You can also use specific software or firewalls to block unwanted data packets and filter the traffic to your server. For example, some firewalls can detect and block attacks targeting certain ports or protocols. Ensuring that your server is up-to-date with the latest security patches and updates is also essential to prevent compression attacks. In conclusion, by recognizing the signs and implementing proper preventive measures, you can secure your website from compression attacks and safeguard your website from data theft and other cyber attacks.
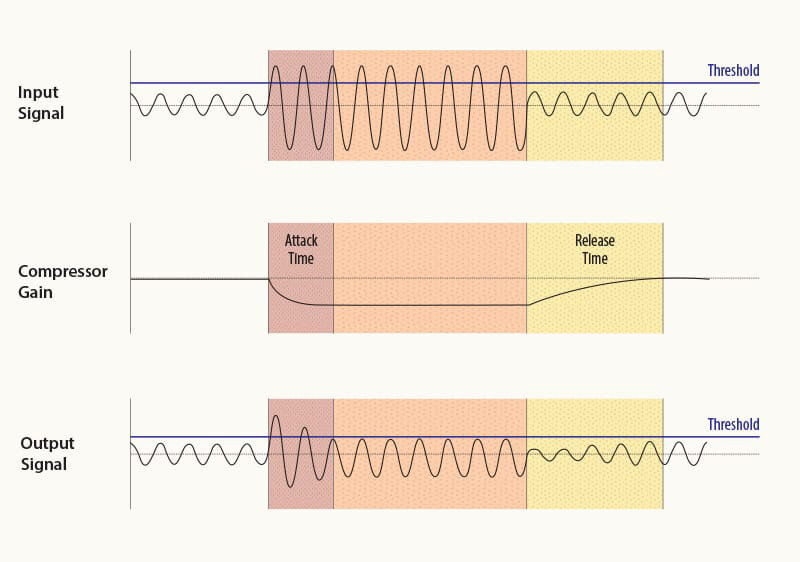
Credit: www.production-expert.com
Frequently Asked Questions On Compression Attack Explained
How Does Compressor Attack Work?
Compressor attack is a type of cyber attack that targets audio files. It works by introducing an extra layer of sound that is imperceptible to the human ear, but can significantly reduce the quality of the original audio. This technique can be used to target confidential conversations or to interfere with audio broadcasts.
What Is Compression And What Does It Do?
Compression is a process of reducing the size of a file or data without losing its quality. It eliminates redundancies and irrelevant information to make the file smaller. It can save storage, speed up data transfer and improve overall performance.
What Is Attack On A Compressor And In What Units Is It Measured?
An attack on a compressor refers to any damage or faults that prevent it from functioning optimally. The capacity of a compressor is measured in units of BTUs (British Thermal Units) or horsepower (HP) and its energy usage is measured in kilowatts (kW).
Why Do Compressors Make Things Louder?
Compressors make things louder because they reduce the dynamic range of audio signals. By decreasing the volume of louder sounds, compressors can amplify quieter sounds, resulting in a more consistent and therefore perceived louder sound overall.
Conclusion
A compression attack is a malicious tactic used by cybercriminals to exploit vulnerabilities of data storage systems. By compressing large amounts of data into smaller packages, attackers can bypass security measures and gain access to sensitive information. To prevent such attacks, it is important for individuals and businesses to implement strong security measures, regularly update software and firewalls, and educate themselves on the latest cybersecurity threats.
With these precautions in place, we can all work towards a safer and more secure digital world.